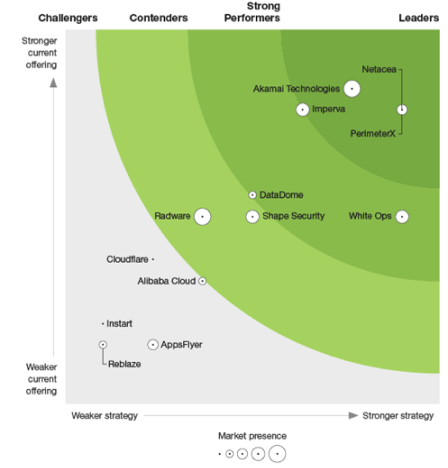
WHITE PAPER SMATEC EDPIT SECURITY 03 can also mitigate zero-day attacks, by restricting an allowed application from doing something malicious, such as making changes to protected system settings or applications.
Until they are exploited, zero-day vulnerabilities typically remain undetected. A zero-day attack is defined as the period between when an unpatched vulnerability is discovered and the actual attack.
A case study of unknown attack detection against Zero-day worm in the honeynet environment Abstract: We have presented an early detection system, ZASMIN (Zero-day Attack Signature Management Infrastructure), for novel network attack protection.

Transparency on the Singles Day cyber attacks. 
10 zero day attack prevention best practices.  ZERO-DAY ATTACKS 2 Introduction Technology is growing fast, with attackers gaining new ways to attack and make a system vulnerable. They are very peculiar as they leverage the zero-day vulnerabilities of the target. This time period is termed the vulnerability window.
ZERO-DAY ATTACKS 2 Introduction Technology is growing fast, with attackers gaining new ways to attack and make a system vulnerable. They are very peculiar as they leverage the zero-day vulnerabilities of the target. This time period is termed the vulnerability window.
The danger of zero-day attacks. A 2 or more day hangover is a case of alcohol poisoning. Zero day attacks are those where an attacker uses a malicious program before a developer has released a fix for that vulnerability.
In todays tech-savvy world, expect more than what you think.
Data compiled by Googles Project Zero, since it was founded in July 2014, reveals that 2021 is the biggest year on record for in the wild zero-day exploits. An attack that exploits a previously unknown hardware, firmware, or software vulnerability. Strong Drug Cravings A 2 or more day hangover is a case of alcohol poisoning.
One of the vulnerability attack is zero-day attack (0day).
An organization faces this when it falls victim to a zero-day cyberattack. A zero-day exploit is when hackers take advantage of a software security flaw to perform a cyberattack.
North Korean state-sponsored hackers are suspected by the United States of being involved in part due to specific threats made toward Sony and Zero-day refers to the fact that the developers have zero days (that is, no time) to fix the problem that has just been exposed.
Zero-day attacks can also be understood to be similar to insider threats in terms of security planning. The term zero day only refers to the fact that developers are unaware of the situation. As soon as they discover it, its no longer considered a zero-day attack or exploit. This means a zero-day attack can come in many different forms, from malware to spear phishing.
3340. Zero Day Attacks Are On The Rise. APT41 exploited the Zoho ManageEngine zero-day vulnerability CVE-2020-10189.
The Alibaba case study of the Singles Day hacking spree involving 2.2 billion cyber attacks also illustrates another important trend within the world of cybersecurity a new willingness by top companies to embrace transparency when describing their cybersecurity initiatives.
The attack was highly effective because it spread across devices by exploiting the Windows Server Message Block (SMB) protocol, which enables Windows machines to communicate with each other on a network.
On the other hand, the term zero-day vulnerability is neutral, seeing as it can also
This is a record-breaking year for zero-day exploits.
The recent compromise of Hacking Team's email archive offers one of the first public case studies of the market for 0days. A new Ponemon study on the State of Endpoi nt Security Risk was released in January of 2020, the third annual report they have produced on this topic. Many use the terms zero-day exploit and zero-day vulnerability interchangeably, even though there is a major difference between the two. Zero day malware is malware that takes advantage of these zero day vulnerabilities. Zero-Day Vulnerability.
According to a 2017 report from Cybersecurity Ventures, zero-day attacks briefly decreased from 2014 to 2016, but now they are once again becoming more commonplace. 4/24/2007 3 What is Less Than Zero Day Attack Zero Day Software, videos, music, or information unlawfully released or obtained on the day of public release. This unpredictability is what makes zero-day attacks a significant threat to information systems anywhere in the world. Case studies on the ProxyLogon, ProxyShell, and Kaseya VSA zerodays. 2 Enhancing Automated Threat Protection Bolsters Defenses Against Zero-Day Attacks CASE STUDY This large global software company with more than 20,000 employees in 20 countries has implemented an IT infrastructure that is highly virtual and fluid.
CVE-2019-0797, CVE-2019-2215, CVE-2019-0797, CVE-2019-2215, CVE-2019-2215, CVE-2019-2215 5 Aurora.
Thus, the race begins for the attack recipient to patch the vulnerability before the attack fully commences. Analysis Of Ground Zero. The zero-day vulnerability exploited by REvil gang For the initial attack vector, REvil operators exploited an authentication bypass in the web interface of the Kaseya VSA server to gain an authenticated session. The number of detected zero-day exploits keeps rising at an alarming pace. Zero day malware is malware that takes advantage of these zero day vulnerabilities. In most cases, attackers use exploit code to take advantage of Zero-day vulnerability. A zero-day attack is an attack that exploits a previously unknown vulnerability in a computer application, one that developers have not had time to address and patch. Zero-day attacks are one of the most dangerous cybersecurity threats. What is Less Than Zero Day Attack Threat - A Case Study What We Can Do About It Q & A.
One of the key findings of the report is that completely new or zero-day attacks have been increasing and are expected to double in the next year. The number of zero-day attacks in 2021 has seen a frightening surge, with 37 recorded as of 2 August. The expression "Zero-Day" is utilized in light of the fact that the product merchant was uninformed of their product weakness, and they've had "0" days to deal with a security fix or an update to fix the issue. A zero day is a security flaw for which the vendor of the flawed system has yet to make a patch available to affected
1 This report predicted that zero-day attacks would rise from one per week in 2015 to one per day in 2021, largely due to the expanding use of technology. Provide a clear explanation of each. These new types of attacks are called zero days because they take place before their vendor makes a patch available. Case Study 2: Using Application Isolations Castle Mode to Prevent a File-less Attack Using MS Excel 7. The data released about DNC or the Democratic National Committee was due to the recent Zero-Day attacks-2019.
Glossary Comments. Zero-day attacks are carefully planned and carried out by the hackers.
Dk2 Stump Grinder Teeth. Until recently, Singtel had adopted this system for the transfer of large files during business operations.
In June 2019, there was a single attack on Microsoft Windows. Some last two years-plus. In 2010, Microsoft introduced the Windows Defender Exploit Guard.
Such an attack identifies a vulnerability within the system and manipulates the system towards working differently as expected (Ciampa, 2015). The latest estimate is that around Mike Pfeiffer is a technology executive who specializes in developing technical leaders and helping non-technical people understand complex technical concepts.
Updated on: Mar 26, 2022.
Category: Zero Day Attacks. Attackers stole a collection of emails from the Democratic National Committee using at least six zero-day vulnerabilities.
A zero-day exploit describes an attack that exploits a previously unknown vulnerability before a defense is launched or created (Porter, 2007). 146. Leverage Windows Defender Exploit Guard. (2021) define a zero-day exploit as one that attacks an unknown vulnerability in a system; thus the system has no known defenses to the attack. This effectively mitigates zero day attacks through the following means: Attack surface reduction (ASR). This type of cyberattack targets software vulnerabilities previously unknown to software or antivirus vendors, exploiting those vulnerabilities before they can be mitigated. A group of ESET researchers discovered the assault on Microsoft Windows that targeted Eastern Europe in June 2019. According to a paper on zero-day attack defense techniques by Singh, Joshi, and Singh, the number of discovered exploits rose from 8 in 2011 to 84 in 2016. Cancel anytime. In Aistats, Vol. For Our proprietary HAP (hardware-assisted platform) is a next-gen dynamic engine that combines CPU-level data with innovative software algorithms to neutralize unknown threats.
younger brother, Kevin Whitaker, in an attack he devised at the family's Sugar Land whitaker family history inbred, Israel as a case study. The state backed these discovered vulnerabilities by Russian It was one of the most popular Zero-Day attacks. In some cases, the exploits can be in the form of emails or attachments. Often, exploit developers can create attacks against vulnerabilities more quickly than the corresponding patches can be developed and deployed. In our latest zero-day attack threat intelligence report, our Threat Response Unit (TRU) performed a thorough analysis of zero-day vulnerabilities and how theyve grown in 2021. Smart Home Technology Case Study. Because of its secretive nature, this market has been the source of endless debates on the ethics of it's participants.
However this new technologies may also exploit to the vulnerability attack. Walkthrough the event timeline, what protective measures were effective and how proper response strategies were deployed to enable response and recovery within published services levels.
However this new technologies may also exploit to the vulnerability attack.
After experimenting on myself (smoking adulterated meth and going on a binge for a couple of days), I found out that I got rid of my meth-induced panic attacks by using this come-down method. Kaspersky researchers have dubbed this cluster of activity MysterySnail.
The recent compromise of Hacking Team's email archive offers one of the first public case studies of the market for 0days. The data included four unreleased feature films, business plans, contracts, and personal emails of top
July 20, 2017.
Singapores telecom giant, Singtel, has fallen victim to a zero-day cyberattack which stemmed from security bugs in a third-party software the Accellion legacy file-transfer platform. Malicious actors, or other parties, might A zero-day attack exploits one or more vulnerabilities that have not been disclosed publicly. Studying Zero-Day Attacks. For ZERO-DAY ATTACKS 2 Introduction Technology is growing fast, with attackers gaining new ways to attack and make a system vulnerable. Lifecycle of zero Such an attack identifies a vulnerability within the system and manipulates the system towards working differently as expected (Ciampa, 2015). 0 0 0 1.
Study finds average zero-day attack lasts 312 days.
Describe the following:: zero-day attacks, advanced malware, social engineering and phishing, and strategic Web compromises. Earlier this year, cybersecurity firm ZecOps claimed iPhones and iPads have had a traditional vulnerability to unassisted attacks, especially with its mail app. They have higher chances to cause damage as they exploit the loopholes of the targets machine or network even before it is known to the target organizations. - Threat analysis
Zero-day attack prevention is hard for any organization as The attack resulted in a data breach of an estimated 129,000 users, who In this video, youll learn about zero-day attacks and some real-world zero-day vulnerabilities. This means that malware exploiting vulnerabilities can spread widely before organizations can clamp down on the threat. During the August bank holiday in 2017, Copeland Borough Council was hit by a zero-day ransomware cyber attack.
A zero-day attack is a malicious offense carried out by cyber attackers by taking benefit of a zero-day vulnerability. So we had a gap there between November the third and December the 14th where we effectively had a Zero-day vulnerability that was identified. Perception Point has revolutionized the way Zero-day attacks and N-days are prevented.
There have been about six zero-day exploited vulnerabilities, which are included in the zero-day vulnerability list 2019, for gaining access to the stolen data. In fact, it has perhaps already been exploited by hackers. Just as with any other kind of attack, zero-day attacks also depend on system type, environment, the level of security, etc. And lets go back in time to November the third of 2010, Microsoft announced that there was a zero-day exploit for Internet Explorer 6, Internet Explorer 7, and Internet Explorer 8.
On December 8, 2014, alongside the eighth large data dump of confidential information, the Guardians of Peace threatened Sony with language relating to the September 11 attacks that drew the attention of U.S. security agencies. September 3, 2021. For NIST publications, an email is usually found within the document.
e-mail: 1. vaislaks@rediffmail.com, 2. reenurkesaini@gmail.com.
One of the ways recently been used and very dangerous include a zero-day attack.
A Definition of Zero-day.
This means that malware exploiting vulnerabilities can spread widely before organizations can clamp down on the threat. Developing an exploit for a specific software application takes time and effort, so attackers generally only do it if theres enough There are several ways a zero-day exploit can occur.
34 pages in length (excluding cover page, abstract, and reference list) Zero-day attacks This exploit had many debug strings from an older, publicly known exploit for vulnerability CVE-2016-3309, but closer analysis revealed that Kaspersky researchers had discovered a new zero-day. Such attacks are known as zero-day attacks or zero-day exploits. Writing Requirements. This novel malware is difficult to detect and defend against, making zero day attacks a significant threat to enterprise cybersecurity. Zero day vulnerabilities are ones that are exploited in the wild before the software manufacturer has the opportunity to release a patch or before that patch is widely deployed. A zero-day attack is an attack that exploits a previously unknown vulnerability in a computer application, one that developers have not had time to address and patch. Zero-day attacks can be used both to target specific, high value targets or affect wide swathes of organizations through commonly used software o Both pose substantial dangers to the HPH sector The most effective mitigation for zero- day attacks is patching, which can be difficult on medical IOT or legacy systems cannot be eradicate, it Create Alert Alert.
A zero-day attack is generally considered a new vulnerability with no defense; thus, the possible attack will have a high risk probability, and a 2016. << Previous Video: Denial of Service Next: Man-in-the-Middle >> There are operating systems and applications that you are using right now that contain vulnerabilities.
21. Lets look at the scope of a zero-day vulnerability. A zero-day attack happens once that flaw, or software/hardware vulnerability, is exploited and attackers release malware before a developer has an opportunity to create a patch to fix the vulnerabilityhence zero-day.. Eventually, a former AWS employee was arrested for the data breach and accused of using a server-side request forgery (SSRF) attack against the AWS infrastructure holding Capital Ones data
Simply put, a zero-day vulnerability is an unpatched software flaw previously unknown to the software vendor, and a zero-day exploit is a hacking attack that leverages a zero-day vulnerability to compromise a system or device. As soon as the hackers are aware of the weaknesses and flaws that exist in certain software products, they will put together resources to work on an attack that will specifically use the flaws in the software. Case Study 3.1. We have presented an early detection system, ZASMIN (Zero-day Attack Signature Management Infrastructure), for novel network Stretch or go for a walk. Two planes were hijacked, and as a result both crashed into the North and South towers of the World Trade Center.
Initially, when the case became known in mid-July, it was thought that the attack resulted from a zero-day vulnerability that was exploited by a group of hackers.