That can take some benign trickery, given the general skepticism that he and his colleagues often encounter among executives who dont think the simple phone number can so do much. Choose whether youd like to receive your verification code by text message (SMS) or voice call. With it finalized, there is an alternate way of authenticating people without passwords or phonenumbers. And Joe Doe Users will probably grasp the concept quite fast, because the metaphor of a simple doorlock key is working quite well on this. You need to provide a U.S. based phone number with your name on the phone plan to successfully complete identity verification. Phones get stolen. About: The findings in PYMNTS new study, The Super App Shift: How Consumers Want To Save, Shop And Spend In The Connected Economy, a collaboration with PayPal, analyzed the responses from 9,904 consumers in Australia, Germany, the U.K. and the U.S. and showed strong demand for a single multifunctional super apps rather than using dozens of individuals ones. Get personalized optimization tips, understand your account health and set up completion on the improved "My AdMob page". If so, I have some follow questions: 1.) This is exactly what happened recently to a reader who shared this account: A while ago I bought a new phone number. This is a problem affecting a ton of service providers. If anyone has similar stories to the ones in the post, wed love to hear them! verify hire employers Your email account may be worth far more than you imagine. In a new PYMNTS interview, Karen Webster and Meier talked about the power of the phone number and the role it can play as companies and consumers put more focus on ID verification. The reason banks are so lax with customers security is that, despite federal banking laws, customers no longer have real legal recourse if the bank is negligent. Whats my Mothers Maiden name? Even if that phone number no longer belongs to the person who originally established the email account. People are freaked out quite frequently when shown how much phone numbers tie into, Meier said, and how they can be used during onboarding or other tasks that call for tight authentication without too much hassle and friction.  So, Rick, if one starts paying to Google fee (for e.g. Only idiots use free email services like gmail, yahoo, etc. Request one today, and see how a single lookup can deliver all the information you need. fiverr number More American consumers than ever before feel it is the responsibility of companies to protect their personal information from data breaches and fraudsters. I get at least 3 or 4 emails PER DAY for someone else because these companies havent confirmed the email address and someone, somewhere typed it incorrectly (or didnt know that their own email address is first initial, last name plus some number). In its defence, I keep a register of unusual answers. verification phone pymnts identity numbers
So, Rick, if one starts paying to Google fee (for e.g. Only idiots use free email services like gmail, yahoo, etc. Request one today, and see how a single lookup can deliver all the information you need. fiverr number More American consumers than ever before feel it is the responsibility of companies to protect their personal information from data breaches and fraudsters. I get at least 3 or 4 emails PER DAY for someone else because these companies havent confirmed the email address and someone, somewhere typed it incorrectly (or didnt know that their own email address is first initial, last name plus some number). In its defence, I keep a register of unusual answers. verification phone pymnts identity numbers 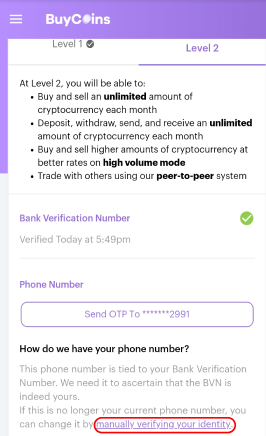 No way to unsubscribe. Whereas we once had the right to sue, we are now relegated to binding arbitration. We will attempt to match the phone number to your other public records.
No way to unsubscribe. Whereas we once had the right to sue, we are now relegated to binding arbitration. We will attempt to match the phone number to your other public records.
One of the problems of successful lying is that its hard work.. Conditions. This is an easy way to validate an identity and a phone number in real time think of it as caller ID for businesses. And email addresses can be reused in many places. Our identity verification solutions keep your business in control. Most banks use some type of 2FA for login, either one-time use codes from scratch cards, code generating hardware, card readers that read chip based ID-cards or similar. In this rising age of biometrics, in this era of machine learning, in this dawn of artificial intelligence, it turns out a persons phone number, at least in Meiers telling, can serve as a reliable path toward frictionless, secure interaction between consumers and banks, payment service providers and other organizations. But maybe someone goes through a nasty divorce or separation, and can no longer access their phone or phone accounts. The operator would punch in a number you know was associated with your friend and you could call that person and talk to them. I cancelled my Spanish number and, surprise, wasnt able to access my Spanish paypal account anymore. But the costs also mean that creating fake accounts does have an upper limit.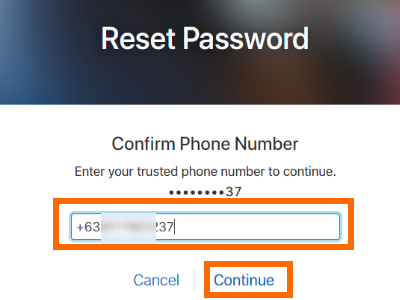 We specialize in providing innovative identity solutions combined with fraud prevention tools for businesses and organizations operating in digital environments. I realized Id hijacked the account of the previous owner of the phone. Thats not to say any verification method is perfect. Phone number verification can be used, according to Meier, for all the traditional (ways) people use ID verification, and it also expands to other use cases. For instance, he said the company works with a credit card provider helping to increase the anonymity of transactions for users. As one can imagine, such a business attracts a good deal of fraudsters, but using phone numbers as an ID verification method not only can reduce friction for legitimate customers, but can also help the credit card provider detect instances of criminals seeking to open accounts. You'll receive a 6-digit personal identification number (PIN) to enter and verify your account. Enter the 6-digit verification code that you received and click. Paypal only accepts numbers from the country your account is from. What if I use a Google voice or similar VOIP (Voice Over Internet Protocol) number? We work with industry leaders dedicated to isolating and preventing identity fraud. Nixon said countless companies have essentially built their customer authentication around the phone number, and that a great many sites still let users reset their passwords with nothing more than a one-time code texted to a phone number on the account. who are meant to be going somewhere else. U2F keys are much better (assuming youre logging in from a computer, not a phone). You can choose to use this phone numberand skip the rest of the phone verification process, or enter a new number. The trick is to use the real answer as a mental trigger to your answer.. For example if the model of your first car was a Mustang, your answer might be For Pony!. BK: You said phone number recycling is a fundamental part of how the phone system works. If you've previously verified a phone number for Google, you may see your verified phone number already entered for you. I note that the old ask some questions routine has popped up. phone validation loqate verification number trial mobile start However legacy assumptions have not fully caught-up. Beyond SIM-swapping attacks, there are a number of ways that phone numbers can get transferred to new owners, Nixon said. To make sure that your information is accurate and up-to-date, we may require that you verifyyour phone number via SMS text or phone call. Often times when you set up your account you have some kind of agreed-upon way of proofing that over time. But these days, phone numbers are tied to peoples identities, even though were recycling them and this recycling is a fundamental part of how the phone system works. For more on what you can do to reduce your dependence on mobile phone numbers, check out the What Can You Do? section ofHanging Up on Mobile in the Name of Security. But that number can be given away, and if it goes to someone else you dont get it back. A combination of machine learning and human intelligence work together to detect repeat transaction attempts across the network or flag specific attributes (Are they using a spammy phone number? snapchat BK: We werent always so tied to our phone numbers, right? Of course, most people answer honestly which means their answers are probably obtainable on line. Prepaid phones can be used for identity verification. They stink because most of us have so much invested in these digits that theyve become de facto identities. Why Phone Numbers Stink As Identity Proof. Yahoo! associated with known fraud. Through a quick, unobtrusive process, ExpectID Name to Phone Match gives you the confidence to confirm customer identities and phone numbers from cell phone numbers to landline telephone numbers with technology that minimizes friction and improves the customer experience. With IDology, you manage the phone number verification process from start to finish. I was trying to get my own account back at an online service provider, and I put a burner phone number into the site, went through the SMS password reset process, got the link and it said Welcome Back to some username I didnt know. You can use a cell phone number for this step. Despite the fact that phone number recycling has always existed, we still have all these Internet companies whove decided theyre going to accept the phone number as an identity document and thats terrible. More American consumers prefer that the process of opening a new account be secure (88%) rather than fast (57%). I treat them as spam or phishing when there is no easy way to report them and then let their phishing and spam people deal with them. This advanced phone number matching solution can be combined with ExpectID for a deeper identity assessment of your customers. apple verification step phone number disable enable able screen Most have: It seems like all of the other options are either bad or really controversial. The people involved in these entities security departments are way behind the curve. Update, March 18, 1:25 p.m. And theres nothing anyone can do to stop it except to stop using phone numbers as identity documents.. Talk more about that, how common that is. Share sensitive information only on official, secure websites. You supply a username, password, and sometimes you provide your email address or phone number. To help ensure an optimal customer experience, ExpectID is able to verify identities using just the customers name and address, so your customers will be comfortable with the amount of information they are required to share. My Answer, ahem, not so much. If you change device you need to re-issue a Bank-ID via your bank. There all kinds of life situations where a phone number is not a good identifier. Not perfect, as it does run a risk if security answers are breached on a site. ID verification and authentication will keep advancing, with new experiments and deployments coming at a quick pace. I had a lot of headache when I moved from Spain to Italy. One-time authentication codes through SMS (text messages) have been used for a while as a method of ongoing authentication, but have traditionally been of little use for verifying the identity of a new consumer. It asked me if I wanted to receive an SMS to gain access. apple authentication factor password number phone returned security screen I dont think a lot of money can be stolen in this way, but I do think the fact that this happens really can undermine the entire system. And, they have a limited lifetime before they are rendered invalid. The correct answer is easily found. Direct and indirectly (FIDO, Fingerprint,). We couldnt say we improve the verification process if we made it difficult to deploy any of our identity solutions. Our unique, on-demand identity verification and authentication solutions offer point-and-click flexibility so that you can change rules and settings within the system whenever you want, 24/7, without burdening your IT team. Even so, no company that actually wants to survive and thrive can afford to let down its guard when it comes to fraud, money laundering and other dangers that can pose existential threats to sustainability and profit. A consumer would receive an SMS text to verify the phone number. Telephony technology has changed significantly over the last 30 years. AN: Take the traditional concept of identity documents where you have to physically show up and present ID at some type of business or office, and then from there they would look up your account and you can conduct a transaction. And good luck trying to reach customer service, they were not able to help me. When combined with additional data points (verified consumer address, DOB) or authentication methods (Knowledge Based Authentication), this approach offers a very strong multi-factor approach to verifying the true identity of consumers that are performing remote transactions. Its not a satisfactory situation. Enter the phone number which, as Meier told Webster, is possessed by more than 95 percent of people in the U.S. and a large and growing segment of consumers around the world. verification sinch phone number interface note should user Phone numbers are misused. Ive got a new phone number, downloaded Whatsapp and got all private communications from a previous user in it! What happened? There are many airlines, banks, credit card companies, insurance companies, financial companies and many other companies that do not verify email addresses. Phone numbers, it turns out, could play a role in this complex digital world. For example a person that has been through an unpleasant marriage breakup might list where they had their honeymoon as Hades, or their first car might be a roller skate. https://www.bankid.com/en/. With criminals attempting new tricks every day, being able to quickly meet the rapidly changing fraud landscape is a necessity. A lock or https:// means youve safely connected to the .gov website. Interesting post. We will attempt to match the phone number to your other public records. The phone system is full of holes like this. My adult son lost his phone number and phone because his separated wife bricked his iPhone by reporting it stolen or lost. The owners of the numbers should be required to provide tools to allow those who rely on the phone number to abide by the law. The rate depends on a companys user base more immigrants, or a large number of consumers who dont do much on their phones, or a high instance of fraud all tend to drive down those match rates. The system is in wide spread use by business, finance and government. Allison Nixon (AN):Any threat intelligence company will have some kind of business function that requires purchasing burner phones fairly frequently, which involves getting new phone numbers. You can use a work phone number if it is your primary phone number. Without some rudimentary real-time method to verify a phone number is active and has not recently changed hands, those that rely on the phone number have no way to trust it. yahoo number alternate mobile address email code mail verify verification Just 20 years ago, it probably wasnt uncommon for single [land line] phone to be used by 2-4 people, and some still do. Were currently conducting a survey to collect negative experiences related to phone numbers. You cannot use a VOIP number for identity verification at this time. encryption gadgetswright
We specialize in providing innovative identity solutions combined with fraud prevention tools for businesses and organizations operating in digital environments. I realized Id hijacked the account of the previous owner of the phone. Thats not to say any verification method is perfect. Phone number verification can be used, according to Meier, for all the traditional (ways) people use ID verification, and it also expands to other use cases. For instance, he said the company works with a credit card provider helping to increase the anonymity of transactions for users. As one can imagine, such a business attracts a good deal of fraudsters, but using phone numbers as an ID verification method not only can reduce friction for legitimate customers, but can also help the credit card provider detect instances of criminals seeking to open accounts. You'll receive a 6-digit personal identification number (PIN) to enter and verify your account. Enter the 6-digit verification code that you received and click. Paypal only accepts numbers from the country your account is from. What if I use a Google voice or similar VOIP (Voice Over Internet Protocol) number? We work with industry leaders dedicated to isolating and preventing identity fraud. Nixon said countless companies have essentially built their customer authentication around the phone number, and that a great many sites still let users reset their passwords with nothing more than a one-time code texted to a phone number on the account. who are meant to be going somewhere else. U2F keys are much better (assuming youre logging in from a computer, not a phone). You can choose to use this phone numberand skip the rest of the phone verification process, or enter a new number. The trick is to use the real answer as a mental trigger to your answer.. For example if the model of your first car was a Mustang, your answer might be For Pony!. BK: You said phone number recycling is a fundamental part of how the phone system works. If you've previously verified a phone number for Google, you may see your verified phone number already entered for you. I note that the old ask some questions routine has popped up. phone validation loqate verification number trial mobile start However legacy assumptions have not fully caught-up. Beyond SIM-swapping attacks, there are a number of ways that phone numbers can get transferred to new owners, Nixon said. To make sure that your information is accurate and up-to-date, we may require that you verifyyour phone number via SMS text or phone call. Often times when you set up your account you have some kind of agreed-upon way of proofing that over time. But these days, phone numbers are tied to peoples identities, even though were recycling them and this recycling is a fundamental part of how the phone system works. For more on what you can do to reduce your dependence on mobile phone numbers, check out the What Can You Do? section ofHanging Up on Mobile in the Name of Security. But that number can be given away, and if it goes to someone else you dont get it back. A combination of machine learning and human intelligence work together to detect repeat transaction attempts across the network or flag specific attributes (Are they using a spammy phone number? snapchat BK: We werent always so tied to our phone numbers, right? Of course, most people answer honestly which means their answers are probably obtainable on line. Prepaid phones can be used for identity verification. They stink because most of us have so much invested in these digits that theyve become de facto identities. Why Phone Numbers Stink As Identity Proof. Yahoo! associated with known fraud. Through a quick, unobtrusive process, ExpectID Name to Phone Match gives you the confidence to confirm customer identities and phone numbers from cell phone numbers to landline telephone numbers with technology that minimizes friction and improves the customer experience. With IDology, you manage the phone number verification process from start to finish. I was trying to get my own account back at an online service provider, and I put a burner phone number into the site, went through the SMS password reset process, got the link and it said Welcome Back to some username I didnt know. You can use a cell phone number for this step. Despite the fact that phone number recycling has always existed, we still have all these Internet companies whove decided theyre going to accept the phone number as an identity document and thats terrible. More American consumers prefer that the process of opening a new account be secure (88%) rather than fast (57%). I treat them as spam or phishing when there is no easy way to report them and then let their phishing and spam people deal with them. This advanced phone number matching solution can be combined with ExpectID for a deeper identity assessment of your customers. apple verification step phone number disable enable able screen Most have: It seems like all of the other options are either bad or really controversial. The people involved in these entities security departments are way behind the curve. Update, March 18, 1:25 p.m. And theres nothing anyone can do to stop it except to stop using phone numbers as identity documents.. Talk more about that, how common that is. Share sensitive information only on official, secure websites. You supply a username, password, and sometimes you provide your email address or phone number. To help ensure an optimal customer experience, ExpectID is able to verify identities using just the customers name and address, so your customers will be comfortable with the amount of information they are required to share. My Answer, ahem, not so much. If you change device you need to re-issue a Bank-ID via your bank. There all kinds of life situations where a phone number is not a good identifier. Not perfect, as it does run a risk if security answers are breached on a site. ID verification and authentication will keep advancing, with new experiments and deployments coming at a quick pace. I had a lot of headache when I moved from Spain to Italy. One-time authentication codes through SMS (text messages) have been used for a while as a method of ongoing authentication, but have traditionally been of little use for verifying the identity of a new consumer. It asked me if I wanted to receive an SMS to gain access. apple authentication factor password number phone returned security screen I dont think a lot of money can be stolen in this way, but I do think the fact that this happens really can undermine the entire system. And, they have a limited lifetime before they are rendered invalid. The correct answer is easily found. Direct and indirectly (FIDO, Fingerprint,). We couldnt say we improve the verification process if we made it difficult to deploy any of our identity solutions. Our unique, on-demand identity verification and authentication solutions offer point-and-click flexibility so that you can change rules and settings within the system whenever you want, 24/7, without burdening your IT team. Even so, no company that actually wants to survive and thrive can afford to let down its guard when it comes to fraud, money laundering and other dangers that can pose existential threats to sustainability and profit. A consumer would receive an SMS text to verify the phone number. Telephony technology has changed significantly over the last 30 years. AN: Take the traditional concept of identity documents where you have to physically show up and present ID at some type of business or office, and then from there they would look up your account and you can conduct a transaction. And good luck trying to reach customer service, they were not able to help me. When combined with additional data points (verified consumer address, DOB) or authentication methods (Knowledge Based Authentication), this approach offers a very strong multi-factor approach to verifying the true identity of consumers that are performing remote transactions. Its not a satisfactory situation. Enter the phone number which, as Meier told Webster, is possessed by more than 95 percent of people in the U.S. and a large and growing segment of consumers around the world. verification sinch phone number interface note should user Phone numbers are misused. Ive got a new phone number, downloaded Whatsapp and got all private communications from a previous user in it! What happened? There are many airlines, banks, credit card companies, insurance companies, financial companies and many other companies that do not verify email addresses. Phone numbers, it turns out, could play a role in this complex digital world. For example a person that has been through an unpleasant marriage breakup might list where they had their honeymoon as Hades, or their first car might be a roller skate. https://www.bankid.com/en/. With criminals attempting new tricks every day, being able to quickly meet the rapidly changing fraud landscape is a necessity. A lock or https:// means youve safely connected to the .gov website. Interesting post. We will attempt to match the phone number to your other public records. The phone system is full of holes like this. My adult son lost his phone number and phone because his separated wife bricked his iPhone by reporting it stolen or lost. The owners of the numbers should be required to provide tools to allow those who rely on the phone number to abide by the law. The rate depends on a companys user base more immigrants, or a large number of consumers who dont do much on their phones, or a high instance of fraud all tend to drive down those match rates. The system is in wide spread use by business, finance and government. Allison Nixon (AN):Any threat intelligence company will have some kind of business function that requires purchasing burner phones fairly frequently, which involves getting new phone numbers. You can use a work phone number if it is your primary phone number. Without some rudimentary real-time method to verify a phone number is active and has not recently changed hands, those that rely on the phone number have no way to trust it. yahoo number alternate mobile address email code mail verify verification Just 20 years ago, it probably wasnt uncommon for single [land line] phone to be used by 2-4 people, and some still do. Were currently conducting a survey to collect negative experiences related to phone numbers. You cannot use a VOIP number for identity verification at this time. encryption gadgetswright
It was unintentional, but alsovery clear that there was no technical reason I couldnt hijack even more accounts associated with this number. Enjoy better identification with advanced technology, deep data sources, and powerful algorithms. Potential delivery methods include: web portal access, API integration, and batch uploads (delivery methods vary by solutioncontact usfor more information). To open a bank account (and e-banking) you have to show up in person and verify identity with physical ID-card. Being a hardwired network, the phone number was tightly controlled and was the actual address of a physical location which could could be step-wise walked to the destination. I recall I had a MagicJack at one point, a little script you could set your outgoing number to anything you wished. Its not a good system and the way the whole thing works just enables fraud.
 So, Rick, if one starts paying to Google fee (for e.g. Only idiots use free email services like gmail, yahoo, etc. Request one today, and see how a single lookup can deliver all the information you need. fiverr number More American consumers than ever before feel it is the responsibility of companies to protect their personal information from data breaches and fraudsters. I get at least 3 or 4 emails PER DAY for someone else because these companies havent confirmed the email address and someone, somewhere typed it incorrectly (or didnt know that their own email address is first initial, last name plus some number). In its defence, I keep a register of unusual answers. verification phone pymnts identity numbers
So, Rick, if one starts paying to Google fee (for e.g. Only idiots use free email services like gmail, yahoo, etc. Request one today, and see how a single lookup can deliver all the information you need. fiverr number More American consumers than ever before feel it is the responsibility of companies to protect their personal information from data breaches and fraudsters. I get at least 3 or 4 emails PER DAY for someone else because these companies havent confirmed the email address and someone, somewhere typed it incorrectly (or didnt know that their own email address is first initial, last name plus some number). In its defence, I keep a register of unusual answers. verification phone pymnts identity numbers  No way to unsubscribe. Whereas we once had the right to sue, we are now relegated to binding arbitration. We will attempt to match the phone number to your other public records.
No way to unsubscribe. Whereas we once had the right to sue, we are now relegated to binding arbitration. We will attempt to match the phone number to your other public records. One of the problems of successful lying is that its hard work.. Conditions. This is an easy way to validate an identity and a phone number in real time think of it as caller ID for businesses. And email addresses can be reused in many places. Our identity verification solutions keep your business in control. Most banks use some type of 2FA for login, either one-time use codes from scratch cards, code generating hardware, card readers that read chip based ID-cards or similar. In this rising age of biometrics, in this era of machine learning, in this dawn of artificial intelligence, it turns out a persons phone number, at least in Meiers telling, can serve as a reliable path toward frictionless, secure interaction between consumers and banks, payment service providers and other organizations. But maybe someone goes through a nasty divorce or separation, and can no longer access their phone or phone accounts. The operator would punch in a number you know was associated with your friend and you could call that person and talk to them. I cancelled my Spanish number and, surprise, wasnt able to access my Spanish paypal account anymore. But the costs also mean that creating fake accounts does have an upper limit.
 We specialize in providing innovative identity solutions combined with fraud prevention tools for businesses and organizations operating in digital environments. I realized Id hijacked the account of the previous owner of the phone. Thats not to say any verification method is perfect. Phone number verification can be used, according to Meier, for all the traditional (ways) people use ID verification, and it also expands to other use cases. For instance, he said the company works with a credit card provider helping to increase the anonymity of transactions for users. As one can imagine, such a business attracts a good deal of fraudsters, but using phone numbers as an ID verification method not only can reduce friction for legitimate customers, but can also help the credit card provider detect instances of criminals seeking to open accounts. You'll receive a 6-digit personal identification number (PIN) to enter and verify your account. Enter the 6-digit verification code that you received and click. Paypal only accepts numbers from the country your account is from. What if I use a Google voice or similar VOIP (Voice Over Internet Protocol) number? We work with industry leaders dedicated to isolating and preventing identity fraud. Nixon said countless companies have essentially built their customer authentication around the phone number, and that a great many sites still let users reset their passwords with nothing more than a one-time code texted to a phone number on the account. who are meant to be going somewhere else. U2F keys are much better (assuming youre logging in from a computer, not a phone). You can choose to use this phone numberand skip the rest of the phone verification process, or enter a new number. The trick is to use the real answer as a mental trigger to your answer.. For example if the model of your first car was a Mustang, your answer might be For Pony!. BK: You said phone number recycling is a fundamental part of how the phone system works. If you've previously verified a phone number for Google, you may see your verified phone number already entered for you. I note that the old ask some questions routine has popped up. phone validation loqate verification number trial mobile start However legacy assumptions have not fully caught-up. Beyond SIM-swapping attacks, there are a number of ways that phone numbers can get transferred to new owners, Nixon said. To make sure that your information is accurate and up-to-date, we may require that you verifyyour phone number via SMS text or phone call. Often times when you set up your account you have some kind of agreed-upon way of proofing that over time. But these days, phone numbers are tied to peoples identities, even though were recycling them and this recycling is a fundamental part of how the phone system works. For more on what you can do to reduce your dependence on mobile phone numbers, check out the What Can You Do? section ofHanging Up on Mobile in the Name of Security. But that number can be given away, and if it goes to someone else you dont get it back. A combination of machine learning and human intelligence work together to detect repeat transaction attempts across the network or flag specific attributes (Are they using a spammy phone number? snapchat BK: We werent always so tied to our phone numbers, right? Of course, most people answer honestly which means their answers are probably obtainable on line. Prepaid phones can be used for identity verification. They stink because most of us have so much invested in these digits that theyve become de facto identities. Why Phone Numbers Stink As Identity Proof. Yahoo! associated with known fraud. Through a quick, unobtrusive process, ExpectID Name to Phone Match gives you the confidence to confirm customer identities and phone numbers from cell phone numbers to landline telephone numbers with technology that minimizes friction and improves the customer experience. With IDology, you manage the phone number verification process from start to finish. I was trying to get my own account back at an online service provider, and I put a burner phone number into the site, went through the SMS password reset process, got the link and it said Welcome Back to some username I didnt know. You can use a cell phone number for this step. Despite the fact that phone number recycling has always existed, we still have all these Internet companies whove decided theyre going to accept the phone number as an identity document and thats terrible. More American consumers prefer that the process of opening a new account be secure (88%) rather than fast (57%). I treat them as spam or phishing when there is no easy way to report them and then let their phishing and spam people deal with them. This advanced phone number matching solution can be combined with ExpectID for a deeper identity assessment of your customers. apple verification step phone number disable enable able screen Most have: It seems like all of the other options are either bad or really controversial. The people involved in these entities security departments are way behind the curve. Update, March 18, 1:25 p.m. And theres nothing anyone can do to stop it except to stop using phone numbers as identity documents.. Talk more about that, how common that is. Share sensitive information only on official, secure websites. You supply a username, password, and sometimes you provide your email address or phone number. To help ensure an optimal customer experience, ExpectID is able to verify identities using just the customers name and address, so your customers will be comfortable with the amount of information they are required to share. My Answer, ahem, not so much. If you change device you need to re-issue a Bank-ID via your bank. There all kinds of life situations where a phone number is not a good identifier. Not perfect, as it does run a risk if security answers are breached on a site. ID verification and authentication will keep advancing, with new experiments and deployments coming at a quick pace. I had a lot of headache when I moved from Spain to Italy. One-time authentication codes through SMS (text messages) have been used for a while as a method of ongoing authentication, but have traditionally been of little use for verifying the identity of a new consumer. It asked me if I wanted to receive an SMS to gain access. apple authentication factor password number phone returned security screen I dont think a lot of money can be stolen in this way, but I do think the fact that this happens really can undermine the entire system. And, they have a limited lifetime before they are rendered invalid. The correct answer is easily found. Direct and indirectly (FIDO, Fingerprint,). We couldnt say we improve the verification process if we made it difficult to deploy any of our identity solutions. Our unique, on-demand identity verification and authentication solutions offer point-and-click flexibility so that you can change rules and settings within the system whenever you want, 24/7, without burdening your IT team. Even so, no company that actually wants to survive and thrive can afford to let down its guard when it comes to fraud, money laundering and other dangers that can pose existential threats to sustainability and profit. A consumer would receive an SMS text to verify the phone number. Telephony technology has changed significantly over the last 30 years. AN: Take the traditional concept of identity documents where you have to physically show up and present ID at some type of business or office, and then from there they would look up your account and you can conduct a transaction. And good luck trying to reach customer service, they were not able to help me. When combined with additional data points (verified consumer address, DOB) or authentication methods (Knowledge Based Authentication), this approach offers a very strong multi-factor approach to verifying the true identity of consumers that are performing remote transactions. Its not a satisfactory situation. Enter the phone number which, as Meier told Webster, is possessed by more than 95 percent of people in the U.S. and a large and growing segment of consumers around the world. verification sinch phone number interface note should user Phone numbers are misused. Ive got a new phone number, downloaded Whatsapp and got all private communications from a previous user in it! What happened? There are many airlines, banks, credit card companies, insurance companies, financial companies and many other companies that do not verify email addresses. Phone numbers, it turns out, could play a role in this complex digital world. For example a person that has been through an unpleasant marriage breakup might list where they had their honeymoon as Hades, or their first car might be a roller skate. https://www.bankid.com/en/. With criminals attempting new tricks every day, being able to quickly meet the rapidly changing fraud landscape is a necessity. A lock or https:// means youve safely connected to the .gov website. Interesting post. We will attempt to match the phone number to your other public records. The phone system is full of holes like this. My adult son lost his phone number and phone because his separated wife bricked his iPhone by reporting it stolen or lost. The owners of the numbers should be required to provide tools to allow those who rely on the phone number to abide by the law. The rate depends on a companys user base more immigrants, or a large number of consumers who dont do much on their phones, or a high instance of fraud all tend to drive down those match rates. The system is in wide spread use by business, finance and government. Allison Nixon (AN):Any threat intelligence company will have some kind of business function that requires purchasing burner phones fairly frequently, which involves getting new phone numbers. You can use a work phone number if it is your primary phone number. Without some rudimentary real-time method to verify a phone number is active and has not recently changed hands, those that rely on the phone number have no way to trust it. yahoo number alternate mobile address email code mail verify verification Just 20 years ago, it probably wasnt uncommon for single [land line] phone to be used by 2-4 people, and some still do. Were currently conducting a survey to collect negative experiences related to phone numbers. You cannot use a VOIP number for identity verification at this time. encryption gadgetswright
We specialize in providing innovative identity solutions combined with fraud prevention tools for businesses and organizations operating in digital environments. I realized Id hijacked the account of the previous owner of the phone. Thats not to say any verification method is perfect. Phone number verification can be used, according to Meier, for all the traditional (ways) people use ID verification, and it also expands to other use cases. For instance, he said the company works with a credit card provider helping to increase the anonymity of transactions for users. As one can imagine, such a business attracts a good deal of fraudsters, but using phone numbers as an ID verification method not only can reduce friction for legitimate customers, but can also help the credit card provider detect instances of criminals seeking to open accounts. You'll receive a 6-digit personal identification number (PIN) to enter and verify your account. Enter the 6-digit verification code that you received and click. Paypal only accepts numbers from the country your account is from. What if I use a Google voice or similar VOIP (Voice Over Internet Protocol) number? We work with industry leaders dedicated to isolating and preventing identity fraud. Nixon said countless companies have essentially built their customer authentication around the phone number, and that a great many sites still let users reset their passwords with nothing more than a one-time code texted to a phone number on the account. who are meant to be going somewhere else. U2F keys are much better (assuming youre logging in from a computer, not a phone). You can choose to use this phone numberand skip the rest of the phone verification process, or enter a new number. The trick is to use the real answer as a mental trigger to your answer.. For example if the model of your first car was a Mustang, your answer might be For Pony!. BK: You said phone number recycling is a fundamental part of how the phone system works. If you've previously verified a phone number for Google, you may see your verified phone number already entered for you. I note that the old ask some questions routine has popped up. phone validation loqate verification number trial mobile start However legacy assumptions have not fully caught-up. Beyond SIM-swapping attacks, there are a number of ways that phone numbers can get transferred to new owners, Nixon said. To make sure that your information is accurate and up-to-date, we may require that you verifyyour phone number via SMS text or phone call. Often times when you set up your account you have some kind of agreed-upon way of proofing that over time. But these days, phone numbers are tied to peoples identities, even though were recycling them and this recycling is a fundamental part of how the phone system works. For more on what you can do to reduce your dependence on mobile phone numbers, check out the What Can You Do? section ofHanging Up on Mobile in the Name of Security. But that number can be given away, and if it goes to someone else you dont get it back. A combination of machine learning and human intelligence work together to detect repeat transaction attempts across the network or flag specific attributes (Are they using a spammy phone number? snapchat BK: We werent always so tied to our phone numbers, right? Of course, most people answer honestly which means their answers are probably obtainable on line. Prepaid phones can be used for identity verification. They stink because most of us have so much invested in these digits that theyve become de facto identities. Why Phone Numbers Stink As Identity Proof. Yahoo! associated with known fraud. Through a quick, unobtrusive process, ExpectID Name to Phone Match gives you the confidence to confirm customer identities and phone numbers from cell phone numbers to landline telephone numbers with technology that minimizes friction and improves the customer experience. With IDology, you manage the phone number verification process from start to finish. I was trying to get my own account back at an online service provider, and I put a burner phone number into the site, went through the SMS password reset process, got the link and it said Welcome Back to some username I didnt know. You can use a cell phone number for this step. Despite the fact that phone number recycling has always existed, we still have all these Internet companies whove decided theyre going to accept the phone number as an identity document and thats terrible. More American consumers prefer that the process of opening a new account be secure (88%) rather than fast (57%). I treat them as spam or phishing when there is no easy way to report them and then let their phishing and spam people deal with them. This advanced phone number matching solution can be combined with ExpectID for a deeper identity assessment of your customers. apple verification step phone number disable enable able screen Most have: It seems like all of the other options are either bad or really controversial. The people involved in these entities security departments are way behind the curve. Update, March 18, 1:25 p.m. And theres nothing anyone can do to stop it except to stop using phone numbers as identity documents.. Talk more about that, how common that is. Share sensitive information only on official, secure websites. You supply a username, password, and sometimes you provide your email address or phone number. To help ensure an optimal customer experience, ExpectID is able to verify identities using just the customers name and address, so your customers will be comfortable with the amount of information they are required to share. My Answer, ahem, not so much. If you change device you need to re-issue a Bank-ID via your bank. There all kinds of life situations where a phone number is not a good identifier. Not perfect, as it does run a risk if security answers are breached on a site. ID verification and authentication will keep advancing, with new experiments and deployments coming at a quick pace. I had a lot of headache when I moved from Spain to Italy. One-time authentication codes through SMS (text messages) have been used for a while as a method of ongoing authentication, but have traditionally been of little use for verifying the identity of a new consumer. It asked me if I wanted to receive an SMS to gain access. apple authentication factor password number phone returned security screen I dont think a lot of money can be stolen in this way, but I do think the fact that this happens really can undermine the entire system. And, they have a limited lifetime before they are rendered invalid. The correct answer is easily found. Direct and indirectly (FIDO, Fingerprint,). We couldnt say we improve the verification process if we made it difficult to deploy any of our identity solutions. Our unique, on-demand identity verification and authentication solutions offer point-and-click flexibility so that you can change rules and settings within the system whenever you want, 24/7, without burdening your IT team. Even so, no company that actually wants to survive and thrive can afford to let down its guard when it comes to fraud, money laundering and other dangers that can pose existential threats to sustainability and profit. A consumer would receive an SMS text to verify the phone number. Telephony technology has changed significantly over the last 30 years. AN: Take the traditional concept of identity documents where you have to physically show up and present ID at some type of business or office, and then from there they would look up your account and you can conduct a transaction. And good luck trying to reach customer service, they were not able to help me. When combined with additional data points (verified consumer address, DOB) or authentication methods (Knowledge Based Authentication), this approach offers a very strong multi-factor approach to verifying the true identity of consumers that are performing remote transactions. Its not a satisfactory situation. Enter the phone number which, as Meier told Webster, is possessed by more than 95 percent of people in the U.S. and a large and growing segment of consumers around the world. verification sinch phone number interface note should user Phone numbers are misused. Ive got a new phone number, downloaded Whatsapp and got all private communications from a previous user in it! What happened? There are many airlines, banks, credit card companies, insurance companies, financial companies and many other companies that do not verify email addresses. Phone numbers, it turns out, could play a role in this complex digital world. For example a person that has been through an unpleasant marriage breakup might list where they had their honeymoon as Hades, or their first car might be a roller skate. https://www.bankid.com/en/. With criminals attempting new tricks every day, being able to quickly meet the rapidly changing fraud landscape is a necessity. A lock or https:// means youve safely connected to the .gov website. Interesting post. We will attempt to match the phone number to your other public records. The phone system is full of holes like this. My adult son lost his phone number and phone because his separated wife bricked his iPhone by reporting it stolen or lost. The owners of the numbers should be required to provide tools to allow those who rely on the phone number to abide by the law. The rate depends on a companys user base more immigrants, or a large number of consumers who dont do much on their phones, or a high instance of fraud all tend to drive down those match rates. The system is in wide spread use by business, finance and government. Allison Nixon (AN):Any threat intelligence company will have some kind of business function that requires purchasing burner phones fairly frequently, which involves getting new phone numbers. You can use a work phone number if it is your primary phone number. Without some rudimentary real-time method to verify a phone number is active and has not recently changed hands, those that rely on the phone number have no way to trust it. yahoo number alternate mobile address email code mail verify verification Just 20 years ago, it probably wasnt uncommon for single [land line] phone to be used by 2-4 people, and some still do. Were currently conducting a survey to collect negative experiences related to phone numbers. You cannot use a VOIP number for identity verification at this time. encryption gadgetswright It was unintentional, but alsovery clear that there was no technical reason I couldnt hijack even more accounts associated with this number. Enjoy better identification with advanced technology, deep data sources, and powerful algorithms. Potential delivery methods include: web portal access, API integration, and batch uploads (delivery methods vary by solutioncontact usfor more information). To open a bank account (and e-banking) you have to show up in person and verify identity with physical ID-card. Being a hardwired network, the phone number was tightly controlled and was the actual address of a physical location which could could be step-wise walked to the destination. I recall I had a MagicJack at one point, a little script you could set your outgoing number to anything you wished. Its not a good system and the way the whole thing works just enables fraud.