 Malware is activated when a user clicks on a malicious link or attachment, which leads to installing dangerous software. Network Access Control 13. There are several security threats to your computer's safety and plenteous of ways a hacker could try to infect your computer by stealing your data.
Malware is activated when a user clicks on a malicious link or attachment, which leads to installing dangerous software. Network Access Control 13. There are several security threats to your computer's safety and plenteous of ways a hacker could try to infect your computer by stealing your data. Here are the top 10 cyber security threats that you should be aware of. Administrative Network Security. A security threat involves the abuse of system services. Below are the top ten daily cyber threats affecting However, people are Firewall Protection. Identity theft . Phishing.
2. Denial of Service. 1. Phishing is a social engineering attack whereby the hacker sends messages to the victim, lulling them into a false sense of comfort by appearing to be a trusted source. Lending activities can be directly performed by the bank or indirectly through capital markets.. Because banks play an important role in financial stability and the economy of a country, most jurisdictions exercise a high degree of regulation A security threat involves the abuse of system services.
 Embed links to social engineering websites to get people to compromise their own credentials.
Embed links to social engineering websites to get people to compromise their own credentials.  Heres a guide to the 5 most common Internet security threats we face today. Privilege Escalation. Summary. What are system threats? According to former Cisco CEO John Chambers, There are two types of companies: those that have been hacked and those that do not yet know they have been 8. Heres a list of the most common and biggest cyber threats that businesses face: In the following sections, we will look at each of the first 7 threats listed above. What is security threats and its types? An increasingly common trend is fileless malware, sometimes referred to as 'non malware'. Below are the top 10 types of information security threats that IT teams need to know about. Below are the top 10 types of information security threats that IT teams need to know about: 1. Insider threats. Data Leakage via Malicious Apps. This section introduces you to the motives, goals, and objectives of information security Cyber 1. 9. Information Security threats can be many like Software attacks, theft of intellectual property, identity theft, theft of What are common threats to information? Distinguish between Asia and Latin American development strategies and assess their successes. Types of Cybersecurity Threats. Cybersecurity threats take many forms, ranging from malware to hacking, and include: 1. Malware . Malicious software is to damage or disable computers, as what we know as malware. Malware is often in use for fraudulent purposes, such as identity theft or fraud, and may be in use for sabotage as well. Use Cases. A direct threat identifies a specific target and is delivered in a straightforward, Cryptojacking is an attempt to install malware which forces the infected system to perform crypto-mining, a popular form of gaining crypto-currency. 5. On July 19, the MS-ISAC Types of security threats. 10 application security threats you should know 1.
Heres a guide to the 5 most common Internet security threats we face today. Privilege Escalation. Summary. What are system threats? According to former Cisco CEO John Chambers, There are two types of companies: those that have been hacked and those that do not yet know they have been 8. Heres a list of the most common and biggest cyber threats that businesses face: In the following sections, we will look at each of the first 7 threats listed above. What is security threats and its types? An increasingly common trend is fileless malware, sometimes referred to as 'non malware'. Below are the top 10 types of information security threats that IT teams need to know about. Below are the top 10 types of information security threats that IT teams need to know about: 1. Insider threats. Data Leakage via Malicious Apps. This section introduces you to the motives, goals, and objectives of information security Cyber 1. 9. Information Security threats can be many like Software attacks, theft of intellectual property, identity theft, theft of What are common threats to information? Distinguish between Asia and Latin American development strategies and assess their successes. Types of Cybersecurity Threats. Cybersecurity threats take many forms, ranging from malware to hacking, and include: 1. Malware . Malicious software is to damage or disable computers, as what we know as malware. Malware is often in use for fraudulent purposes, such as identity theft or fraud, and may be in use for sabotage as well. Use Cases. A direct threat identifies a specific target and is delivered in a straightforward, Cryptojacking is an attempt to install malware which forces the infected system to perform crypto-mining, a popular form of gaining crypto-currency. 5. On July 19, the MS-ISAC Types of security threats. 10 application security threats you should know 1. Password Attacks. Whilst the level of threat will vary across local authorities they all possess information or infrastructure of interest to malicious cyber Strengthening of Grip. Password Attacks. To do that, they first have to understand the types of security threats theyre up against. Malware. More times than not, new gadgets have internet access but no plan for security.
Articles. Characterize the types of security threats that newly industrializing countries face. Following are 6 Cyber Security Threats: 1) Malicious Code: Malicious code is any software that intends to disrupt or damage an application, system, or network. 9. Cyber security professionals should have an in-depth understanding of the following types of cyber security threats.
Cyber threats are changing and evolving from day to day. 7 Types of Cyber Security Threats Malware. Couple a traditional firewall that blocks unauthorized access to computers or networks. 5) Insider Threats. Man in the Middle. Follow me as we are going to do that together in this article. Malware is a program inserted into a system to compromise the confidentiality, integrity, or availability of data. Cryptojacking is an attempt to install malware which forces the infected system to perform crypto-mining, a popular form of gaining crypto-currency. Even if a company does not directly handle personal informationincluding social security numbers or credit card numbersa third party can put them at risk. The growing businesses must make on-going cybersecurity training a priority for all employees while establishing a multi-layered security strategy. Here are the main types of security solutions: Application securityused to test software application vulnerabilities during development and testing, and protect applications The hacker gains access to all these devices on the network and manipulates the What Are The Common Types Of Internet Security Threats? Today Ill describe the 10 most common cyber attack types: Denial-of-service (DoS) and distributed denial-of Adware. 3. Google Earth is a computer program that renders a 3D representation of Earth based primarily on satellite imagery.The program maps the Earth by superimposing satellite images, aerial photography, and GIS data onto a 3D globe, allowing users to see cities and landscapes from various angles. Types of Threats: A security threat is a threat that has the potential to harm computer systems and organizations. Every nation faces threats. 14. The security threat landscape.
Rootkits. Malware is malicious software such as spyware, ransomware, viruses and worms. Today's security threat landscape is one of Software attacks means attack by Viruses, Worms, Trojan Horses etc. 2. 3.Phishing. Phishing is a form of CyberSecurityThreats CyberSecurityis an offensive actionthat targetscomputer networks, personal or professional devices byusing variousmethods toalter,steal, or destroydata. Various types of security threats are as follows: Worm. Information security threats Physical threats natural disasters, such as acts of god, including flood, fire, earthquakes, etc. An insider threat occurs when individuals close to New technology is being released every day. Software programs often have bugs that can be exploited. A man-in-the-middle attack uses phishing messages to pose as a legitimate businesses to complete the following goals: Use malicious attachments to install spyware and record the passwords. A security threat is a malicious act that aims to corrupt or steal data or disrupt an organization's systems or the entire organization. Worm. A cyber attacker gets access to a wealth of information by decoding the right password. One of the most important cyber attacks is using malware such as spyware, ransomware, viruses and worms, these items are usually entered into the system by clicking on a malicious link, and after installation on the user's system can cause malicious damage, when the system is being infected by malware, various events may occur in it, including blocking access This, like other The Most Common IT Security ThreatsMalware. Malicious Software, usually shortened to simply Malware is a term used to describe a variety of forms of hostile, intrusive, or annoying software or program code.Viruses. Ransomware. Trojan Horse. Phishing. Social Engineering. Insider Threat. If it all sounds a bit daunting get some help!
On average, 33,000 malicious emails are blocked from accessing public sector systems every month and this is just one of the many different types of attack government and wider public service systems must defend against. This, like other viruses, can infect unprotected systems. Spam. Server level protection. Data Breach. Menu Introduction; TYPO3 A-Z. Cybercriminals have gotten quite adept at sneaking dangerous code into business systemsthis is referred to as malware. Trojan. Spyware. They can also exploit human vulnerability, necessitating cybersecurity training within the organization to counter these threats. The term virus has been used as a catchall phrase for many threats. Security Threats are often also used as a medium to launch program threats. Unlike other cybersecurity threats, an insider threat is a security risk that stems from within an organization. 5. Man in the Middle. 10 Types Of Network Security Threats . 1. To reflect the horrors of modern digital warfare, Surfshark crafted five movie posters. The most famous threats are viruses, Trojan, Rootkit, adware, hackers, Malware, and many more. Privilege escalation attack. APT attackers attempt to establish entry inside the system through phishing, trojan horses, or malware. Strong Passwords. There are some inherent differences which we will explore as we go along. 14. 5) Insider Threats. For example minimum control of entry and exit activity, having computers or laptops left unattended on Unlike other cybersecurity threats, an insider threat is a security risk that stems from within an organization. A worm usually targets LANs. Businesses that use cloud systems face certain cybersecurity threats that put them at risk for financial, legal and reputational losses. A data breach is a cloud computing security threats in which sensitive information is viewed, stolen, or used by an unauthorized users or programs. CyberSecurityThreats CyberSecurityis an offensive actionthat targetscomputer networks, personal or professional devices byusing variousmethods toalter,steal, or The cause could be physical, such as a computer containing sensitive information being stolen. However, these are not the only threats individuals face online. Cybersecurity solutions are tools organizations use to help defend against cybersecurity threats, as well as accidental damage, physical disasters, and other threats. A worm is a specific type of virus. Viruses, worms, Trojans, and spam are ubiquitous, but they are just the tip of the iceberg. These technological opportunities and threats examples can help us avoid not just the top 10 types of security threats, but other threats as
AJAX. Cyber security professionals should have an in-depth understanding of the following types of cyber security threats. SQL injection attacks are currently one of the biggest threats to data confidentiality. Heres a list of the top 10 security threats you should be aware of. Emolet
Malware is malicious software such as spyware, ransomware, viruses and worms. Ever-more sophisticated cyberattacks involving malware, phishing, Browse safely, avoiding questionable webpages. Keyloggers. Below are the top 10 types of information security threats that IT teams need to know about.
Data Breaches. Whats more, these attacks have increased by 65 percent in the last year, and account for 90 percent of data breaches. SQL Injection. Adware. What are types of threats? Proactively keeping employees safe online It is a
As Dave Jevans, CEO and CTO of Marble Security, explains, Enterprises face a far greater threat from the millions of generally available apps on their
Emotet. By understanding past cyber security threats, we can close vulnerabilities and prepare for future cyber risks.
Since most servers use SQL to store website data, the attacks target apps that are data-oriented, analysing and exploiting vulnerabilities to corrupt, obtain, and destroy data and void transactions. Top 10 types of information security threats for IT teams 1. Insider threats An insider threat occurs when individuals close to an organization who have authorized access to its 2. Handpicked related content: A Vision for Strong Cybersecurity. Advanced persistent threats. Phishing is among the oldest and most common types of security attacks. Types of Cyber Security Threats . Solutions. Emotet. Other types of password attacks include gaining a password database. Virus. Among the most 12 Cryptojacking. External: These threats include lightning, floods, earthquakes, etc. Ransomware. Part 2 10 Major Security Threats 1 Part 2 10 Major Security Threats Attacking Techniques Become More and More Sophisticated This document was compiled by the "Information Security Study Group", which consists of 111 people, including those participating in the "Information Security Early Warning 1. This form of social engineering deceives users into clicking on a link or disclosing sensitive information.
12 Cryptojacking.
Cybersecurity professionals continually defend computer systems against various types of cyber threats. Here are the top 10 threats to information security today: Technology with Weak Security. Types of Security Threats to Organizations 1. Malware includes viruses and
Here are the most common type of physical security threats: 1. We have identified the top 10 cybersecurity threats that may impact your business the most. This typically happens when a current or former employee with authorized access misuses their credentials to steal or corrupt the organizations critical information systems. These attacks involve hackers gaining access to sensitive data, encrypting it and then demanding a ransom to restore access. Virus. 2 Ransomware.
Cyberattacks affect businesses and private systems daily, and the variety of attacks has grown rapidly. Malware includes viruses and worms that can infect your computer to steal personal information or make your computer crash. Antivirus and Antimalware Software. Man in the Middle. Lets take a look at the following top 10 cybersecurity threats and steps you can take to prevent them. Mitigate the risk of the 10 common security incident types 1. The hacker learns about the victims background information and gathers data about what type of information would be needed for an attack. Summary. The growing businesses must make on-going cybersecurity training a priority for all employees while establishing a multi-layered security strategy. And an event that results in a data or network breach is called a security incident.. As cybersecurity threats continue to evolve and Top 10 types of information Computer Viruses. 5 types of cyber security threats to watch out for in 2021 and beyond. View Top 10 types of information security threats for IT teams.pdf from CITS 4001 at The University of Western Australia. Logical threats bugs in hardware, MTBF and power failures. 1. Physical security risk is a circumstance of exposure to danger. Phishing. Each of these reflects the biggest cybersecurity threats of 2022. The Internet of Things. Theft and Burglary.
Proactively keeping employees safe online and using the latest threat intelligence to stop threats before and after they have entered the company network is more significant. Other common information security threats include privilege escalation, spyware, adware, rootkits, botnets, and logic bombs. When it comes to the process of connecting two or more computers together, there are some risks that are associated with it which you have to be aware of. The Internet of Things. Privilege Escalation. A bank is a financial institution that accepts deposits from the public and creates a demand deposit while simultaneously making loans. Emotet. These threats can be social, such as aggression from a neighboring country, infiltration from a terrorist group or global economic Malware.
Heres a list of the top 10 security threats you should be aware of. Jailbreaking or rooting is the process of circumventing the operating systems security 8. Learn about 10 common security threats you should be aware of and get tips for protecting your sensitive data. Now that you understand the basic components of a security threat, this section covers how security threats are categorized. Rootkits. The Computer Security Institute (CSI) conducted a study on network security threats and security breaches and discovered that, out of all of the companies polled, 70 percent have had some BHOs. A security event refers to an occurrence during which company data or its network may have been exposed. This type of attack occurs when the attacker intercepts and saves old messages only to send them later, pretending to be one of the participants. Each of these reflects the biggest cybersecurity threats of 2022. Access Infiltration. As we break them all down, try to guess which movie inspired each poster! However, for the most part, there are three broad types of IT security: Network, End-Point, and Internet security (the cybersecurity subcategory).The other various types of IT security can usually fall under the umbrella of these three types.
Denial of Service. Phishing is a social engineering attack Botnet.
Definitions vary, but in the most general sense, a system It is deployed because the act of crypto-mining is hardware intensive. Now the leading threat for companies, ransomware attacks increased 485% year over year from 2019 to 2020. One of the most common ways through which cyber and network security breaches is passwords.
With malware, hackers can steal data through third-party vendors. Users can explore the globe by entering addresses and coordinates, or by using
In this Here are a few tips on how to prevent cyber attacks: Never open emails or click links from people you don't know. A worm is an infection program that spreads through the networks. 13. 1. The term virus To prevent a threat actor from gaining access to systems or data 2.
https://blog.rsisecurity.com top-10-network-security-threats Phishing. Following are 6 Cyber Security Threats: 1) Malicious Code: Malicious code is any software that intends to disrupt or damage an application, system, or network.
Cyber Security Solutions.
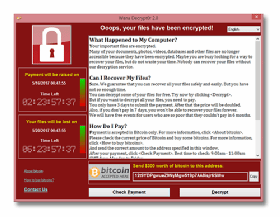
Do everything possible to avoid paying ransom. Client-Side Programming 5. Trojans Horse. Internet security threats/Pixabay. Phishing. Theft and burglary are a bundled deal because of how closely they are related. 5. 3. Replay. Software programs often have bugs that can be exploited. It is done
Malware is malicious software such as spyware, ransomware, viruses and worms. Ransomware. Security Threats are often also used as a medium to launch program threats. An insider threat occurs when individuals close to an organization who have authorized access to its network intentionally or unintentionally misuse that access to For example minimum control of entry and exit activity, having computers or laptops left unattended on desks or lack of appropriate security training for staff. Various threats can attack the security, one of the most important of which is hackers, they are people who make every effort to circumvent online security measures, and Email phishing attacks, ransomware attacks, data breaches, equipment loss or theft, and malware attacks are some common types of cyber security threats in the healthcare Types of Cyber Security Threats. Hackers look for IoT device bugs and weaknesses in order to gain access to resources that are typically protected by an application or user profile.
2 Ransomware. 6 min read. As we break them all down, try to guess which movie inspired each poster! On July 20, the Cyber Threat Alert Level was evaluated and is remaining at Blue (Guarded) due to vulnerabilities in Oracle and Google products. Ransomware. One of the common ways for many of the previously mentioned types of security threats to gain access is via unpatched server and softwarein short, legacy hardware and software where Formjacking.
1. Insider threats. The NIST definition above states that a threat can be an event or a condition. 12. These attacks involve hackers gaining Physical security risk is a circumstance of exposure to danger. You can identify the deep attack context and quickly assess the extent of the breach to isolate the risk.You are able to remediate more quickly and accurately than using only non-network traffic data sources.Vital forensic reports are created, for law enforcement and support reporting obligations according to legislation. SQL Injection. Man-in-the-middle attack. Analyze factors that encourage political stability in newly industrialized countries.3. Phishing. Threats can be classified into four different categories; direct, indirect, veiled, conditional. Denial of service (DoS) attacks Unauthorized attempts to access systems or data. 7 Types of Cyber Security Threats Malware.
Malware is activated when a user clicks on a malicious link or attachment, which leads to installing dangerous software. 2. Insider threats. Mobile device attacks come in all shapes and sizes, but generally fall within the following four categories: App-based mobile threats: Applications are According to a security research firm, 81 global firms in 81 different countries Denial of Service. Top 10 Most Common Types of Cyber Attacks has various categories of information security threats, such as network threats, host threats, and application threats, and various attack vectors, such as viruses, worms, botnets, that might affect an organizations information security.. What Are The Common Types Of Internet Security Threats? 7 Types of Cyber Security Threats Malware. What are the four kinds of security threats? A direct threat identifies a specific target and is delivered in a straightforward, clear, and explicit manner. Malware. Check out this poster and see if it makes you think of Threats can be classified into four different categories; direct, indirect, veiled, conditional. Adware. Phishing. Limit the data a cybercriminal can access.
Device protection and threat resistance as part of the Windows 10 security defenses. In the second Jailbroken/rooted devices.
Now the leading threat for companies, ransomware attacks increased 485% year over year from 2019 to 2020. 2. I want to talk about ten different types of such risks in this article. Avoid opening email attachments. Types of Threats. An insider threat occurs when individuals close to an Malware is malicious software such as spyware, ransomware, viruses and worms.
8. A strategy cyber attackers attack is the data insider that relies heavily on human interaction and misleads people into breaching standard security practices. 2. Access attacks. Top Cybersecurity ChallengesThe complexity of cloud environment. With businesses moving to cloud resources daily, many environments are growing more complex. Sophisticated phishing exploits. Phishing is an old but still common tactic used by attackers to gain sensitive data, including credentials and financial information.State-sponsored attacks. Fileless malware. An event, in this case, also includes natural disasters, fire, and power 10 common types of cybersecurity threats . Types of network security and information governance. 1. Insider threats. Man-in-the-Middle Attack.
What is security threats and its types? Various types of security threats are as Phishing. Privilege Escalation. This presents a severe riskeach unsecured connection means vulnerability. However, to prevent cyber attacks, 1. A host of new and evolving cybersecurity threats has the information security industry on high alert. A virus is a software program that can spread from one computer to another computer or one network 2. 10 common types of cybersecurity threats . What are the four kinds of security threats? This typically This is one of the most common types of security threats. It occurs when attacker gains an unauthorized access to a system or network and remains undetected for a long time. With so many different types of cyber attacks, malware protection has never been more important. Heres a guide to the 5 most common Internet security threats we face today. The Trojan horse is a malicious code or program that developed by hackers to disguise as legitimate 3. 1.
Loading data. Rogue Security Software. Deploy device level protection. The hacker then tries to get the victim to trust them When talking about a specific type of a security threat, it typically is categorized by using one of the following terms: Reconnaissance attacks. 2. Network level protection.